Blog Summary:
This blog dives deep into the concept of DevSecOps, where DevOps meets security, setting the stage for a safer and more efficient development process. After laying out the compelling advantages of this approach, we transition into discussing the challenges you may face in adopting DevSecOps.
Table of Content
These challenges, however, are not insurmountable—our article offers a set of practical guidelines that serve as a roadmap for successful implementation. To make this journey even smoother, we close with a handpicked list of tools designed to facilitate the seamless incorporation of security into your DevOps cycle. Get ready for an all-encompassing guide to making your software development more secure and efficient.
An overview of the importance of implementing DevOps and DevSecOps not just for the software development lifecycle (SDLC) but also for the cloud, containers, and serverless computing platforms.
DevOps Security has emerged as a cornerstone for bolstering the SDLC. Incorporating DevOps and DevSecOps is not merely a technical enhancement but a business imperative, extending its significance beyond SDLC to cloud infrastructures, containers, and serverless computing platforms. The size of the DevSecOps market is estimated to go to $30 billion by 2032.

The market is anticipated to see significant potential due to the growing adoption of advanced technologies by small and medium-sized organizations, as well as greater IT modernization activities. This demonstrates a clear trend toward an industry-wide acceptance and investment in DevOps Security, reflecting its critical role in ensuring a secure and efficient software development and deployment process.
Hence, for CTOs and business owners striving for operational excellence and risk mitigation, embracing DevOps Security is not an option but a necessity in achieving a secure, efficient, and competitive edge in today’s fast-paced technological arena.
DevOps Security, commonly known as DevSecOps, is an approach that integrates security practices directly into the DevOps workflow. This strategy aims to embed security into every part of the development lifecycle. Rather than being a separate stage or an afterthought, DevOps Security becomes an integral component of the entire development and deployment process.
This is a key difference between DevOps and Agile, as Agile methodologies may not necessarily focus on embedding security throughout the cycle.
In DevOps security, the main goal is to “shift security left,” meaning that security measures are integrated more closely with the development phase. This ensures early detection and resolution of security vulnerabilities, reducing both the cost and complexity of addressing issues at later stages.
Central to this methodology are DevOps Security Tools, which facilitate automated, continuous monitoring and immediate feedback. These tools are incorporated into the CI/CD pipeline, automating frequent security checks and providing real-time alerts, thus creating a more proactive stance toward security issues.
DevOps Security not only streamlines the software development process but also significantly enhances its security posture. The result is an improved balance between speed, functionality, and security. When comparing DevOps vs Agile, the level of automation and real-time security monitoring in DevOps is often more advanced.
DevOps and DevSecOps both aim to optimize the SDLC, but they have key differences, primarily in the integration of DevOps Security. DevOps focuses on streamlining development and operations to achieve quicker deployments and higher efficiency. DevSecOps, on the other hand, extends these goals to include security measures throughout the lifecycle.
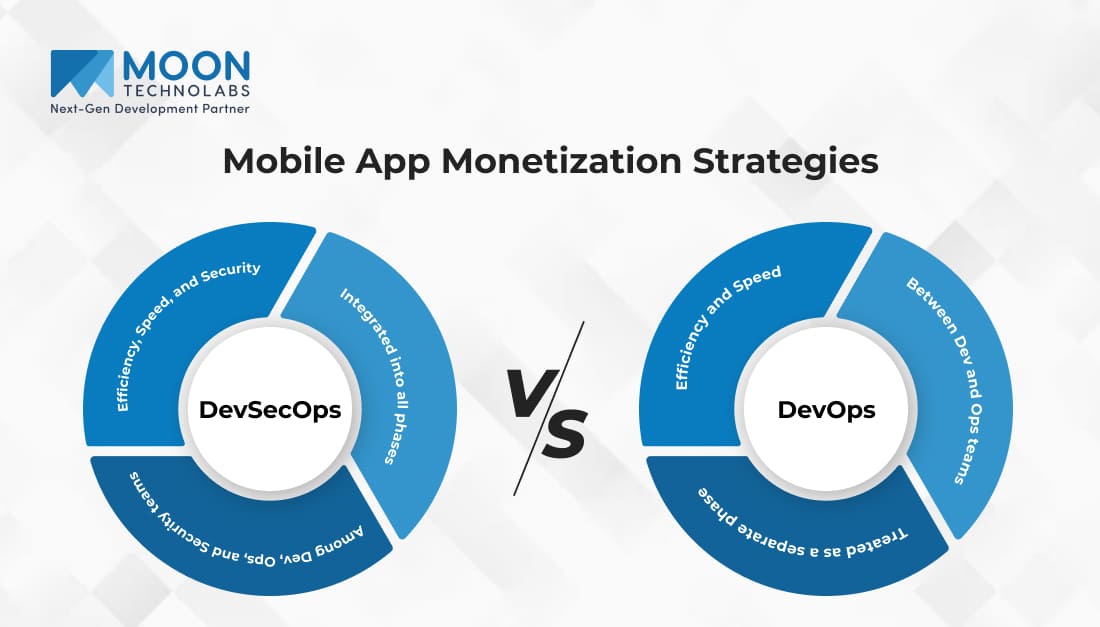
| DevOps | DevSecOps | |
|---|---|---|
| Focus | Efficiency and Speed | Efficiency, Speed, and Security |
| Security | Treated as a separate phase | Integrated into all phases |
| Collaboration | Between Dev and Ops teams | Among Dev, Ops, and Security teams |
DevSecOps incorporates DevOps Security from the planning stage to deployment, making security an integral part of the development process. This results in a more robust, secure end product without sacrificing speed or functionality.
The following sections elucidate the significant benefits of adopting DevSecOps, which seamlessly blends development, operations, and security. This integrated approach optimizes your software development lifecycle, enhancing both efficiency and security.
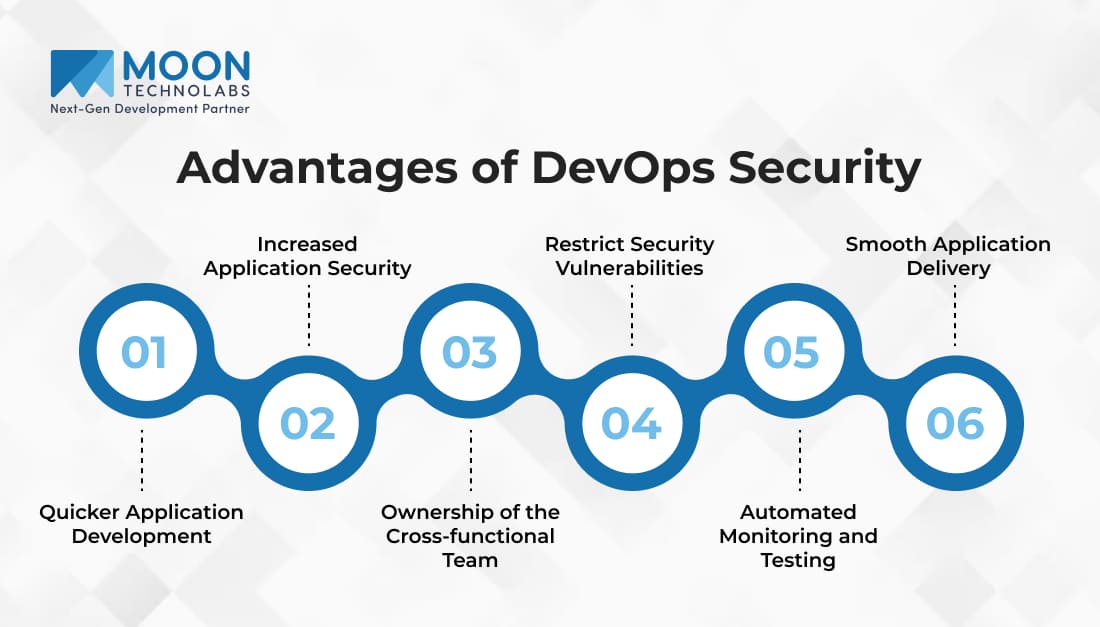
Integrating DevOps security into your development cycle doesn’t just improve security; it can also speed up the development process itself. By automating security checks and incorporating them into the CI/CD pipeline, developers can address vulnerabilities as soon as they occur. This prevents last-minute scrambles to fix issues and ensures that the application can be delivered on schedule.
Implementing security measures through DevOps consulting offers an in-depth strategy for enhancing application security from the initial stages to final deployment. By using proactive methods to identify and address vulnerabilities, robust application security is ensured.
This approach not only protects user data but also fortifies the system against potential breaches. In doing so, it adds an additional layer of security that goes beyond basic compliance requirements, delivering peace of mind for both the development team and end-users.
The ownership model in a DevOps environment often includes not just developers and operations staff but also security experts. Adopting DevOps services that integrate security measures means all stakeholders take part in maintaining and enhancing the security of the application.
This multi-disciplinary approach ensures that security isn’t just the concern of a single team but is a shared responsibility across departments.
By incorporating DevOps security into your CI/CD pipeline, you’re taking proactive steps to minimize the security vulnerabilities that often plague software applications. Source code analysis and security scans become a part of the routine development cycle, allowing your team to catch vulnerabilities early and remedy them before they escalate into bigger issues.
Automation is one of the cornerstones of DevOps, and when you integrate security into this model, you gain the benefit of automated monitoring and testing. Not only does this save time, but it also ensures that security measures are consistently applied across the development and deployment phases. Automation tools can continuously scan for vulnerabilities, giving you an up-to-date understanding of your security posture.
One of the often-overlooked benefits of DevOps security is its impact on the application delivery process. By identifying and addressing security concerns early in the development process, you remove roadblocks that could potentially delay or derail the deployment of the application. This means fewer last-minute scrambles to fix issues, resulting in a smoother, more efficient delivery process for all involved.
Incorporating DevOps security offers an approach that enhances both the security and efficiency of your software development process. By taking these steps, you’re making a significant contribution to creating more secure and reliable applications.
The journey toward robust DevOps security is laden with a variety of challenges that organizations must successfully navigate. From collaboration issues to the modernization of legacy infrastructures, the complexities are many.
Here are the key challenges you should be aware of:
While DevOps security aims to integrate security measures into the DevOps process, one of the major challenges lies in achieving seamless collaboration between development, operations, and security teams.
Each team often has its own set of priorities and tools, which can result in miscommunication or friction. Overcoming this challenge requires a cultural shift towards acknowledging the importance of security within the DevOps framework.
Traditional development cultures may not always be receptive to the new demands posed by integrating security. Database DevOps best practices, for instance, could be seen as a hurdle that slows down development.
This resistance can stymie the effective implementation of security measures. Management needs to play a crucial role in facilitating this cultural shift, emphasizing that security is a shared responsibility.
The use of containers in DevOps adds another layer of complexity to security issues. While containers make it easy to manage and deploy applications, they also pose security challenges.
Databases in DevOps environments that utilize containers must be meticulously configured to prevent unauthorized access. Even then, DevOps database systems running in containers can still be vulnerable to exploits if not adequately secured.
Cloud environments are incredibly useful for DevOps practices due to their scalability and flexibility. However, they bring unique challenges in the realm of DevOps security. Protecting data and applications in the cloud is crucial, and it often involves specialized security protocols that differ from those used in traditional on-premises settings.
Outdated systems can present another set of challenges when adopting DevOps automation services. Legacy infrastructures often lack the capabilities needed to fully implement modern security measures, requiring a transformational approach led by DevOps management.
Adapting or upgrading these older systems is essential for creating a secure DevOps environment. Understanding and addressing these challenges is critical for any organization looking to optimize its DevOps security protocols.
While the road may be filled with obstacles, acknowledging them is the first step in creating a more secure and efficient DevOps environment.
Understanding the intricacies of DevOps security calls for specific best practices. Here are the essential guidelines to enhance your DevOps security measures effectively:
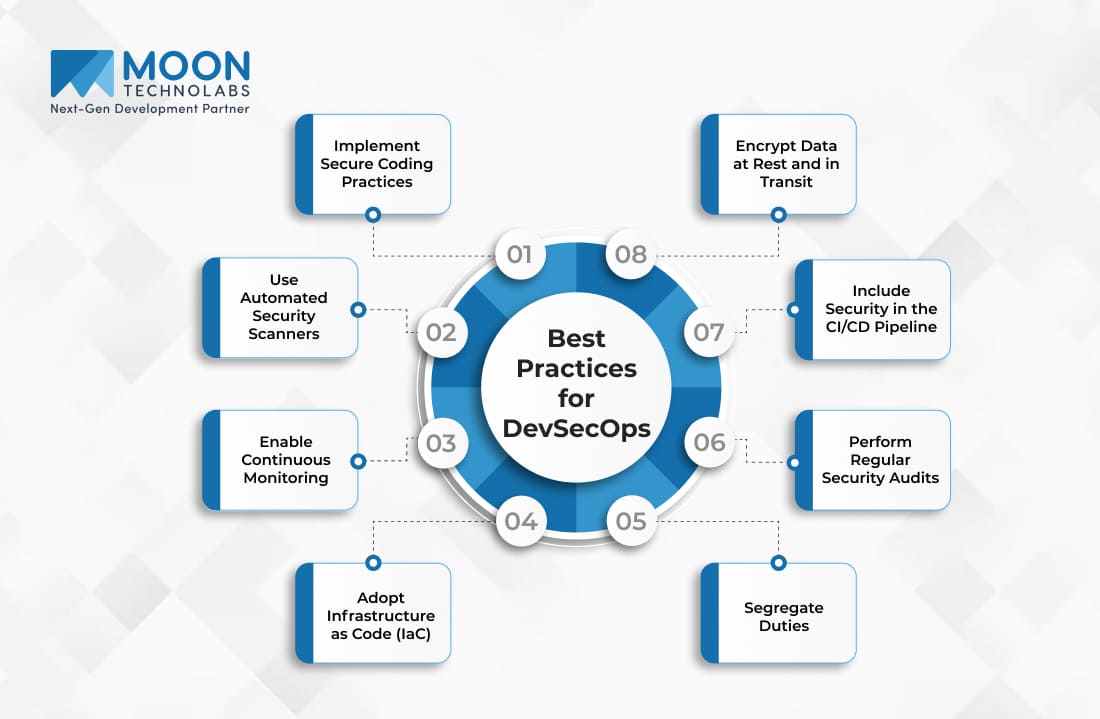
Start with security in mind at the coding phase itself. Incorporating secure coding guidelines ensures that the developers produce code with fewer vulnerabilities. It aligns well with the DevOps principles of security, minimizing risks right from the early stages.
Automated security scanners can identify vulnerabilities before they become a critical issue. These tools integrate seamlessly into DevOps implementation services, allowing developers to catch and fix issues during the development phase.
Always keep an eye on your application and infrastructure. Continuous monitoring tools can alert you to any unusual activities, helping you react quickly to any potential security threats. DevOps services often include these types of monitoring tools.
Infrastructure as Code allows for the programmatic setup, configuration, and management of servers. It enhances DevOps security by allowing you to version-control your infrastructure in the same way you do with your source code.
Split responsibilities among different members or teams to reduce the risk of a single point of failure or insider threats. This is a classic security measure but still holds value within DevOps implementation services.
Don’t just rely on automated tools. Periodic security audits conducted by external DevOps consulting experts can offer invaluable insights into the effectiveness of your security measures.
Including security checks and tests in your Continuous Integration and Continuous Deployment (CI/CD) pipeline ensures that security is an integral part of your development process. This is often recommended as a best practice in DevOps consulting.
Make sure all sensitive data is encrypted, both when it’s stored and when it’s moving from one service to another. Encryption should be a standard feature offered by your DevOps services, ensuring that data leaks and breaches are minimized.
By focusing on these best practices, you can significantly enhance the security posture of your DevOps processes. Whether you are just starting with DevOps or looking to improve existing workflows, these practices can serve as a roadmap for effective DevOps security.
DevOps security encompasses practices, methodologies, and tools to integrate security into your DevOps processes seamlessly. Below are some of the critical tools that play a pivotal role in achieving a secure DevOps lifecycle.

Automated Dynamic Analysis (ADA) is a technique that examines the behavior of applications during runtime to identify security threats and vulnerabilities. By utilizing this method, teams can detect issues that may occur in a live environment, making it an essential tool in the arsenal of DevOps security Tools.
The security of the supply chain is paramount to ensure that every component integrated into the software is free from vulnerabilities. Tools for supply chain security scrutinize third-party components for potential risks, ensuring a secure development environment from the get-go.
Static Code Analysis (SCA) is a method used to analyze source code for potential vulnerabilities and coding errors. Utilizing SCA is a proactive approach to identifying issues early in the development phase, proving to be one of the effective tools for DevOps security.
Interactive Application Security Testing (IAST) combines elements of static and dynamic analysis to identify security vulnerabilities in both code and running applications. This approach provides a more thorough examination of potential security risks within the development lifecycle.
Aqua Security provides a comprehensive platform for securing applications across the entire development lifecycle. With its ability to scan for vulnerabilities and enforce security policies, it’s a valuable addition to any DevOps security toolkit.
Checkmarx offers a suite of solutions to address security concerns within DevOps environments. Its ability to integrate seamlessly with existing DevOps workflows makes it a practical choice for teams looking to bolster their security posture.
Snyk specializes in identifying and fixing vulnerabilities in open-source dependencies. By integrating Snyk into the DevOps pipeline, teams can ensure a more secure code base before deployment.
SonarQube is a platform that is open-source and is utilized for continuously inspecting the quality of code. It offers a thorough analysis of code security, which helps in locating vulnerabilities and finding solutions to fix them.
IriusRisk offers a threat modeling platform that aids in identifying, managing, and mitigating security risks within DevOps processes.
Acunetix specializes in web application security, providing a robust platform to identify a wide range of security vulnerabilities, ensuring a well-rounded approach to integrating security within DevOps practices.
Employing a combination of these DevOps Security Tools can significantly bolster the security posture of your development and operations pipeline. It’s best to consult with a DevOps consulting firm to select the most appropriate tool for your infrastructure.
In the sphere of DevOps security, having a proficient partner like Moon Technolabs can significantly elevate the security protocols within your development and operations pipeline. Our adept team meticulously integrates security measures at every phase, ensuring a robust defense against potential threats.
The synergy between your DevOps practices and our security expertise cultivates a culture of continuous improvement, making your software development journey both innovative and secure. Our collaborative approach at Moon Technolabs not only fortifies your DevOps security but also drives a seamless and efficient workflow, ultimately propelling your projects toward success with a solid security backbone.
01
02
03
Submitting the form below will ensure a prompt response from us.